Planning your IAM strategy is crucial before implementing an identity and access management framework in your business. Your IAM framework is not just a simple piece of software that you buy and install as-is. It’s a complex solution that includes multiple resources, such as new and legacy software, databases, policies, and organizational culture toward security. In fact, an IAM strategy potentially affects all stakeholders in the business.
For building such a complex system and guaranteeing that the business goals will be achieved, you need a solid plan to start with. The planning of your IAM strategy should be based on a deep understanding of the current organizational reality.
This article outlines the steps to create a comprehensive plan to successfully manage and secure digital identities and access to resources. It also points out serious mistakes you should avoid while planning your IAM strategy. Finally, it discusses the pros and cons of outsourcing the implementation of your IAM framework.
Content
- Planning your IAM strategy step by step
- Mistakes to watch out for while planning your IAM strategy
- Planning your IAM strategy: outsource it or not?
Planning your IAM strategy step by step
In the first article of this 2-part series – about the reasons to have an IAM strategy – we saw that creating an effective IAM strategy is crucial for managing and securing your digital identities and access to resources.
By following these 7 steps, you can ensure that your IAM plan supports your business growth and meets your compliance requirements. Whether you are implementing an IAM framework for the first time or looking to improve an existing one, these steps will guide you through the process of planning your IAM strategy.
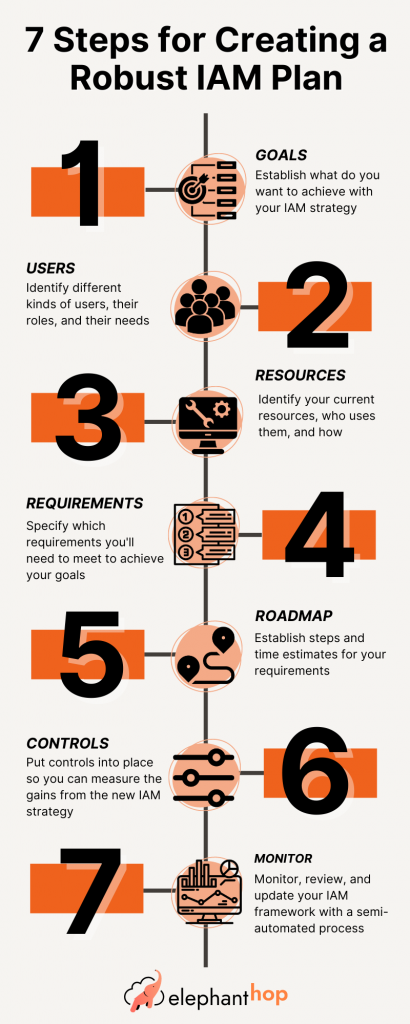
Step 1: Identify your goals
The first step in planning your IAM strategy is to identify your goals. What do you want to achieve with your IAM strategy? Some common goals include reducing risk, improving productivity, and meeting compliance requirements.
It’s important to ask yourself and a representative sample of all the company stakeholders what problems they face related to security, identity, and access. The team responsible for planning your IAM strategy must gather information such as:
- Where and when issues happen
- How they affect people’s productivity and well-being
- What kinds of workarounds people use to circumvent the burdens imposed by the current state of affairs
- How issues and shortcuts affect business security
- How they impair the quality of the products and services offered by the business
The answers to these questions should generate a list of problems that can be solved by the IAM framework to be implemented. You will need to prioritize the problems-solutions list, taking into consideration factors such as cost, potential impacts on the company and on the people involved, and available resources.
Step 2. Identify your users
The next step in planning your IAM strategy is to identify your users. Who will be using your systems and resources, and what level of access do they need? This will help you determine what type of authentication and authorization controls you need to put in place.
Your IAM planning should include a complete identity and access audit. You need to review all current group roles and their authorization statuses. You want to make sure that your IAM strategy implements the zero-trust policy, which is a key feature of robust identity and access management.
This means that all access attempts should be verified and authenticated, regardless of whether the user is inside or outside the company’s network. Trust nothing, verify everything in all three tiers (user, device, and network). This helps to prevent malicious actors from gaining unauthorized access to your systems and data. Our upcoming post on Zero Trust will dive deeper into the methodology.
Step 3. Identify your resources
The next step in planning your IAM strategy is to identify your resources. What systems, data, and other resources do you need to protect? This will help you determine what access controls you need to put in place.
Resource identification may include resources you can leverage during the implementation of your IAM strategy, including human, technical, and external resources. Make sure you consider the architecture of your IT infrastructure. It’s important to understand which resources are the most critical to your business and should be given the highest level of protection.
Step 4. Determine your IAM requirements
Based on your goals, users, and resources, determine what specific requirements you have for your IAM strategy. This may include things such as strong password policies, multi-factor authentication, and role-based access controls.
Other common requirements include keeping compliance with industry standards and with identity and access management best practices. The IAM software is part of the requirements too. It needs to provide the appropriate solutions to all requirements, and it should be able to integrate with your existing systems and processes.
Step 5. Organize your project plan in a roadmap
Once you have identified your goals, users, resources, and requirements, the next step is to turn the project plan into a roadmap. This should include tasks and milestones, resources and timelines, and risk management. The project plan should be realistic, taking into consideration all the constraints, such as budget, time, and resources.
Step 6. Implement your IAM controls
Based on your requirements, implement the appropriate controls to manage and secure your digital identities and access to resources. Controls give the business the ability to assess the success level after the new IAM strategy implementation. They also provide valuable information for continuous monitoring and improvement.
Step 7. Monitor and review your IAM strategy
The last step in your IAM planning is not exactly a step, but an ongoing process. You must define up-front the processes the company is going to use to regularly review and monitor its IAM strategy.
The controls implemented will be used and eventually refined in this maintenance phase. You should rely on the automation features of your IAM tool as much as possible in the monitoring and reviewing process. Remember this is not related to the core business and can be easily overlooked. Ongoing monitoring and maintenance are also important to ensure that the IAM solution continues to meet the needs of the business.
Mistakes to watch out for while planning your IAM strategy
Less attentive or experienced people can easily make some fatal mistakes when creating a plan for an IAM strategy for their business. Some of the riskiest errors are underestimating the usage of external devices, not paying enough attention to de-provisioning users, automating faulty authentication and authorization processes, and not taking peoples’ reactions to the new system into consideration.
Don’t underestimate external devices
Technology keeps running over our ability to catch up with it. Not long ago, work was done at the office on the company’s computers. Then personal notebooks, tablets, and smartphones came into the scene and out of the office. To top it off, the pandemic accelerated the adoption of remote work. It’s easy to overlook the impact of external personal devices on the IAM framework with all these recent changes.
Don’t treat de-provisioning as an afterthought
Usually, smart leaders put a lot of effort into onboarding new employees but don’t have the time or documentation needed for proper termination. However, blocking out the access of people who leave the company is absolutely crucial for a secure identity and access strategy.
Automate the right things
While planning your IAM strategy you have a great opportunity to revise current access and identity processes. Blindly automating poorly designed processes is not the smartest way of using the automation capabilities of your IAM framework.
Ensure buy-in from employees for the changes
People need to understand and buy into the changes that will affect their work. The first step of planning your IAM strategy can be a great opportunity to make people aware of the benefits of the new IAM processes and policies. They will also need support during implementation and this should be taken into consideration when creating your plan.
Planning your IAM strategy: outsource it or not?
One of the most important decisions when planning your IAM strategy is whether to outsource it or to handle it in-house. Handling IAM in-house can offer a number of benefits, such as:
- Control: By handling IAM in-house, you have more control over the process and can ensure that it aligns with your company’s specific needs and goals.
- Customization: An in-house team can tailor the solution to your unique needs and requirements.
- Proprietary knowledge: By handling IAM in-house, your company can retain knowledge and understanding of the IAM solution, which can be useful for future projects and developments.
On the other hand, Control, Customization, and Proprietary Knowledge can all be outsourced and managed through a proper evaluation and discovery by a skilled IAM consultant and integrator. By outsourcing the whole process and in addition to Control, Customization, and Proprietary Knowledge you get:
- Access to expertise: A team of IAM consultants and integrators have the experience and knowledge to help you create a more effective and secure IAM strategy.
- Cost savings: Outsourcing can be more cost-effective than building an in-house team.
- Flexibility: Outsourcing allows you to scale your IAM resources up or down as needed.
Ultimately, the decision to outsource or handle IAM in-house will depend on your company’s specific needs, goals, and resources. If you are still not sure about the best option for you and your company, ElephantHop is here to help. We provide expert guidance and support for businesses looking to implement a robust IAM strategy. Contact us today to learn more about how we can help you plan your IAM strategy.


